
Physical security is one of the key elements in Security besides the human and technology part. The three elements basically linked together in an equal manner where hackers always try to find an.

A lot of companies have reserved more than one domain name for their organization. Multiple of those domain name are not been used for email purpose but are a target for hackers to.

Assume you have a image of an file system that needs to be mounted. This could be on a linux system in case you need to recovering data or for forensics reasons. With.

Sometimes you need to resize your partition of your VPS system when you for example requested additional diskspace. In the below tutorial I resized my VPS hard-disk. Keep in mind that having a.

Vaak wordt door organisaties het bepalen van de scope voor een penetratie test onderschat. Het niet juist scopen van een opdracht kan resulteren in bijvoorbeeld een niet volledige test of dat er onvoldoende.
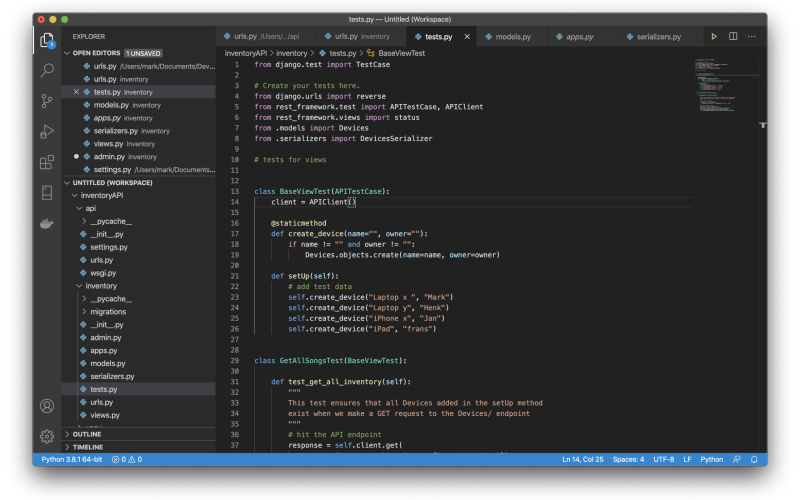
In this blog post, I will introduce how to develop a API Service in Django using Django REST Framework (DRF). In this example you will be introduced to DRF with minimal amount of.
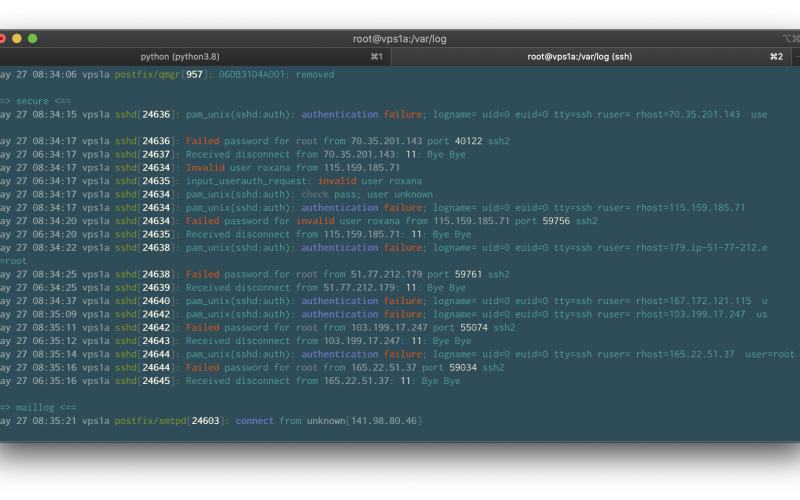
Lot’s of systems on the internet are been hacked trough the use of easy guessable passwords or default credentials. In many cases the source ip address is been hacked the same way. Attackers.

What is Gophish? Gophish is a phishing framework that makes the simulation of real-world phishing attacks dead-simple. The idea behind gophish is simple – make industry-grade phishing training available to everyone. “Available” in.